Difference between revisions of "User:Mauirixxx/pfSense IPSec VPN"
m (→Configuration: starting phase 2) |
m (→Phase 2: done sort of) |
||
| Line 47: | Line 47: | ||
=== Phase 2 === | === Phase 2 === | ||
| − | From the above screen, click on "Show Phase 2 Entries (0)" and expand out the menu, then click on the green "'''+''' Add P2" button. | + | From the above screen, click on "Show Phase 2 Entries (0)" and expand out the menu, then click on the green "'''+''' Add P2" button that appears. |
| + | ==== General Information ==== | ||
| + | * Mode: Tunnel IPv4 | ||
| + | * Local Network: LAN subnet | ||
| + | * NAT/BINAT translation: None | ||
| + | * Remote Network: Network | ||
| + | ** Address (Work): 192.168.10.0/24 | ||
| + | ** Address (Home): 192.168.1.0/24 | ||
| + | * Description: | ||
| + | ** Home: Work LAN | ||
| + | ** Work: Home LAN | ||
| + | ==== Phase 2 Proposal (SA/Key Exchange) ==== | ||
| + | * Protocol: ESP | ||
| + | * Encryption Algorithms: AES128-GCM @ 128 bits | ||
| + | * Hash Algorithms: AES-XCBC (or SHA256 if your CPU doesn't have AES-NI) | ||
| + | * PFS key group: 14 (2048) | ||
| + | * Lifetime: 3600 | ||
| + | ==== Advanced Configuration ==== | ||
| + | * Automatically ping host: set this IP address to a server you run 24/7, this will keep the VPN up 24/7 | ||
| + | |||
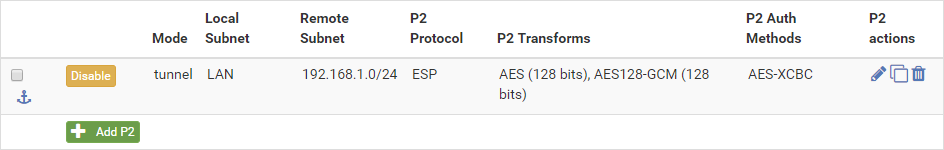
| + | After you hit save, this is what your Phase 2 will look like: | ||
| + | [[File:Phase2-complete.png]] | ||
Revision as of 02:13, 20 July 2019
About
How to setup an ipsec vpn between 2 instances of pfsense using both a static (work) and dynamic ip address (home office). However, a static IP is NOT a requirement.
Software used
- pfSense: https://www.pfsense.org
Requirements
- Dynamic OR static IP address
- A domain name or a free dynamic DNS provider.
- CPU with AES-NI (if your uplink is 20Mbps or faster)
Configuration
I'm going to assume that if you're at this point, you already have a working pfSense configuration at both locations.
Both locations must NOT have the same internal LAN address - meaning both can't be running 192.168.1.x addresses, one can run 192.168.1.x while the other can run 192.168.2.x.
Final note - the VPN configuration on both firewalls will be exactly the same, save for parts that require IP addresses or hostnames.
Let's get started:
- Click on VPN -> IPsec, and on the bottom right, click on the green "+ Add P1" button at the bottom of the screen.
Phase 1
General Info
- Key exchange version: IKEv2
- Internet Protocol: IPv4 (IPv6/Dual stack will work if you're running IPv6 at both sites)
- Interface: WAN (or whatever you named the interface with the public IP address)
- Remote Gateway: this is where you need either your own domain, or a free Dynaimc DNS provider - or manually entering the IP addresses works, users with dynamic IP addresses the "work" location will have to update your IP address manually every time it changes.
- Remote Gateway (home): work.piracyforjesus.xyz
- Remote Gateway (work): home.piracyforjesus.xyz
- Description: put whatever you like or leave blank
Phase 1 Proposal (Authentication)
- Authentication Method: Mutual PSK
- My Identifier: Distinguished name:
- Home: home.piracyforjesus.xyz
- Work: work.piracyforjesus.xyz
- Peer identifier: Peer IP address
- Pre-Shared Key: On one firewall, click generate key, then copy & paste that key to the other firewall
Phase 1 Proposal (Encryption Algorithm)
- Encryption Algorithm:
- Algorithm: AES128-GCM
- Key Length: 128 bits
- Hash: SHA256
- DH Group: 14 (2048)
- Lifetime (Seconds): 28800
Advanced Options
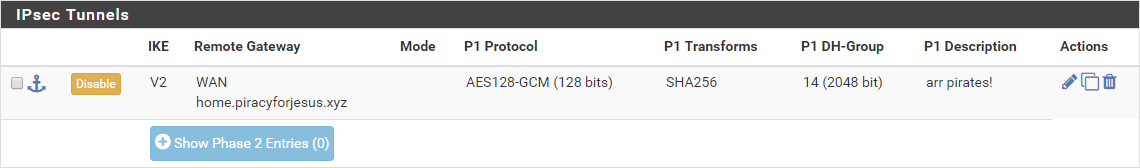
Leave everything defaulted in this section, and click Save. When finished, it should look like this:
Phase 2
From the above screen, click on "Show Phase 2 Entries (0)" and expand out the menu, then click on the green "+ Add P2" button that appears.
General Information
- Mode: Tunnel IPv4
- Local Network: LAN subnet
- NAT/BINAT translation: None
- Remote Network: Network
- Address (Work): 192.168.10.0/24
- Address (Home): 192.168.1.0/24
- Description:
- Home: Work LAN
- Work: Home LAN
Phase 2 Proposal (SA/Key Exchange)
- Protocol: ESP
- Encryption Algorithms: AES128-GCM @ 128 bits
- Hash Algorithms: AES-XCBC (or SHA256 if your CPU doesn't have AES-NI)
- PFS key group: 14 (2048)
- Lifetime: 3600
Advanced Configuration
- Automatically ping host: set this IP address to a server you run 24/7, this will keep the VPN up 24/7
After you hit save, this is what your Phase 2 will look like: